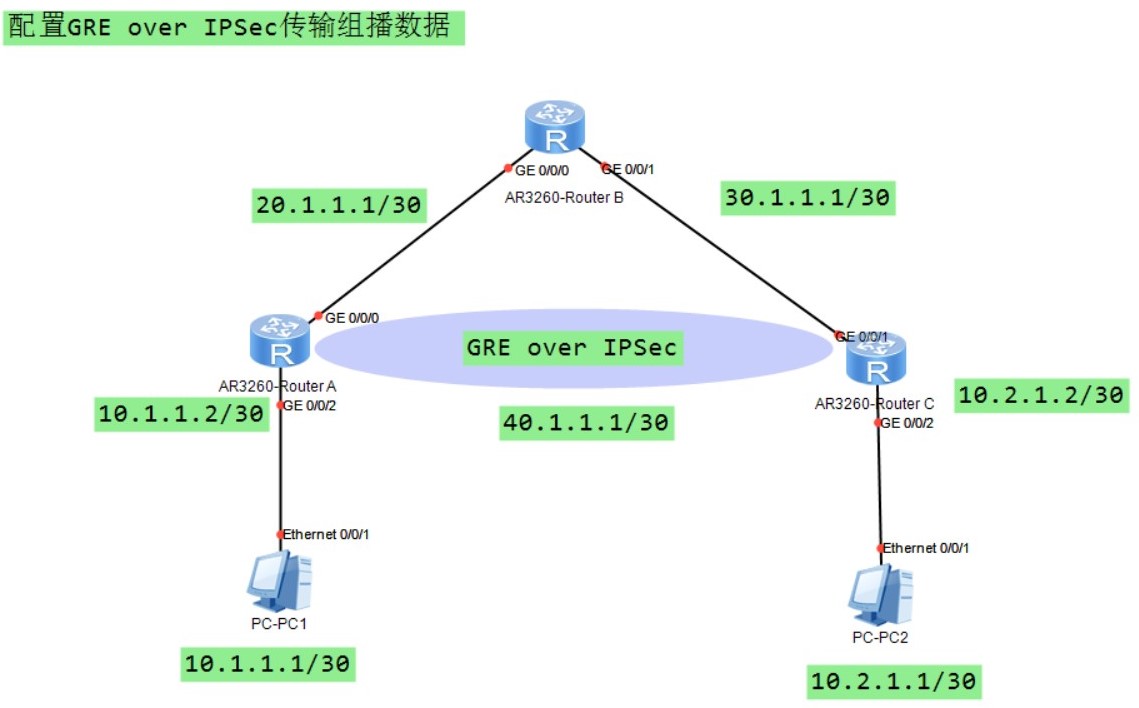
组网需求
- PC2作为组播源,Router A和Router C之间传输组播数据,并要对数据进行IPSec加密
- 由于组播数据无法直接应用IPSec,因此先对组播数据进行GRE封装,在对GRE封装后的报文进行IPSec加密
组网拓扑
配置思路
- 在Router A、Router B、Router C上运行OSPF协议,实现路由器的互通
- 在Router A与Router C 之间建立GRE隧道
- 全局使能组播路由协议,在Tunnel接口下使能PIM DM,在与PC相连的接口使能PIM DM和IGMP
- 在Router A和Router C上建立IPSec隧道,加密GRE封装后的组播报文
配置命令
配置路由器基本功能以及各个接口IP地址
Router A配置
1
2
3
4
5
6
7
8sys
sys Router A
int g0/0/0
ip add 20.1.1.1 30
int g0/0/2
ip add 10.1.1.12 30
int LoopBack 0
ip add 1.1.1.1 32
Router B配置
1
2
3
4
5
6
7
8sys
sys Router B
int g0/0/0
ip add 20.1.1.2 30
int g0/0/1
ip add 30.1.1.2 30
int LoopBack 0
ip add 2.2.2.2 32
Router C配置
1
2
3
4
5
6
7
8sys
sys Router C
int g0/0/1
ip add 30.1.1.1 30
int g0/0/2
ip add 10.2.1.2 30
int LoopBack 0
ip add 3.3.3.3 32
配置OSPF协议,实现路由器的互联互通
Router A配置
1
2
3
4sys
ospf 1 router-id 1.1.1.1
area 0
network 20.1.1.0 0.0.0.3
Router B配置
1
2
3
4
5sys
ospf 1 router-id 2.2.2.2
area 0
network 20.1.1.0 0.0.0.3
network 30.1.1.0 0.0.0.3
Router C配置
1
2
3
4sys
ospf 1 router-id 3.3.3.3
area 0
network 30.1.1.0 0.0.0.3
Router A与Router C之间建立GRE隧道,配置接口地址、源地址、目的地址、隧道协议
Router A配置
1
2
3
4
5
6sys
int Tunnel 0/0/0
ip add 40.1.1.1 30
tunnel-protocol gre
source 20.1.1.1
destination 30.1.1.1
Router C配置
1
2
3
4
5
6sys
int Tunnel 0/0/0
ip add 40.1.1.2 30
tunnel-protocol gre
source 30.1.1.1
destination 20.1.1.1
使能组播路由协议、组管理协议
Router A配置
1
2
3
4
5
6
7sys
multicast routing-enable
int g0/0/2
pim dm
igmp enable
int Tunnel 0/0/0
pim dm
Router C配置
1
2
3
4
5
6
7sys
multicast routing-enable
int g0/0/2
pim dm
igmp enable
int Tunnel 0/0/0
pim dm
配置IPSec(IKE版本为version 1、模式为野蛮模式)
Router A配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32sys
// 保护数据流的ACL匹配本端Tunnel的source、destination地址
acl 3000
rule 0 permit gre source 20.1.1.0 destination 30.1.1.1
quit
// 配置IPSec的参数
ipsec proposal P1
quit
// 配置IKE参数
ike local-name rta
ike peer routerc v1
exchange-mode aggressive
local-id-type name
pre-shared-key simple 12345
remote-name rtc
remote-address 30.1.1.1
quit
// 配置IPSec的策略
ipsec policy policy1 1 isakmp
security acl 3000
ike-peer routerc
proposal P1
quit
// 配置接口使能IPSec策略
int g0/0/0
ipsec policy policy1
quit
Router C配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32sys
// 保护数据流的ACL来匹配本端Tunnel的source、destination地址
acl 3000
rule 0 permit gre source 30.1.1.1 destination 20.1.1.1
quit
// 配置IPSec参数
ipsec proposal P1
quit
// 配置IKE的参数
ike local-name rtc
ike peer routera v1
exchange-mode aggressive
local-id-type name
pre-shared-key simple 12345
remote-name rta
remote-address 20.1.1.1
quit
// 配置IPSec策略
ipsec policy policy1 isakmp
security acl 3000
ike-peer routera
proposal P1
quit
// 接口配置IPSec策略
int g0/0/1
ipsec policy policy1
quit
配置Tunnel转发路由
Router A配置
1
ip route-static 10.2.1.0 30 tunnel 0/0/0
Router C配置
1
ip route-static 10.1.1.0 30 tunnel 0/0/0
查看结果
查看OSPF路由表
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18display ospf routing-table protocol ospf
<Router A>dis ip routing-table protocol ospf
Route Flags: R - relay, D - download to fib
------------------------------------------------------------------------------
Public routing table : OSPF
Destinations : 1 Routes : 1
OSPF routing table status : <Active>
Destinations : 1 Routes : 1
Destination/Mask Proto Pre Cost Flags NextHop Interface
30.1.1.0/30 OSPF 10 2 D 20.1.1.2 GigabitEthernet
0/0/0
OSPF routing table status : <Inactive>
Destinations : 0 Routes : 0
查看GRE隧道状态
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15ping -a 40.1.1.1 40.1.1.2
<Router A>ping -a 40.1.1.1 40.1.1.2
PING 40.1.1.2: 56 data bytes, press CTRL_C to break
Reply from 40.1.1.2: bytes=56 Sequence=1 ttl=255 time=40 ms
Reply from 40.1.1.2: bytes=56 Sequence=2 ttl=255 time=30 ms
Reply from 40.1.1.2: bytes=56 Sequence=3 ttl=255 time=30 ms
Reply from 40.1.1.2: bytes=56 Sequence=4 ttl=255 time=40 ms
Reply from 40.1.1.2: bytes=56 Sequence=5 ttl=255 time=30 ms
--- 40.1.1.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 30/34/40 ms
PC1与PC2可以相互ping通
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16ping 10.2.1.1
PC>ping 10.2.1.1
Ping 10.2.1.1: 32 data bytes, Press Ctrl_C to break
From 10.2.1.1: bytes=32 seq=1 ttl=126 time=15 ms
From 10.2.1.1: bytes=32 seq=2 ttl=126 time=32 ms
From 10.2.1.1: bytes=32 seq=3 ttl=126 time=31 ms
From 10.2.1.1: bytes=32 seq=4 ttl=126 time=16 ms
From 10.2.1.1: bytes=32 seq=5 ttl=126 time=15 ms
--- 10.2.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/21/32 ms
在IPSec两端的设备上看到IKE协商建立,IPSec加密已生效(Router A)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52display ike sa
<Router A>display ike sa
Conn-ID Peer VPN Flag(s) Phase
---------------------------------------------------------------
3 30.1.1.1 0 RD|ST 2
2 30.1.1.1 0 RD|ST 1
Flag Description:
RD--READY ST--STAYALIVE RL--REPLACED FD--FADING TO--TIMEOUT
HRT--HEARTBEAT LKG--LAST KNOWN GOOD SEQ NO. BCK--BACKED UP
display ipsec sa
<Router A>display ipsec sa
===============================
Interface: GigabitEthernet0/0/0
Path MTU: 1500
===============================
-----------------------------
IPSec policy name: "policy1"
Sequence number : 1
Acl Group : 3000
Acl rule : 0
Mode : ISAKMP
-----------------------------
Connection ID : 3
Encapsulation mode: Tunnel
Tunnel local : 20.1.1.1
Tunnel remote : 30.1.1.1
Flow source : 20.1.1.1/255.255.255.255 47/0
Flow destination : 30.1.1.1/255.255.255.255 47/0
Qos pre-classify : Disable
[Outbound ESP SAs]
SPI: 3499190510 (0xd09168ee)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5
SA remaining key duration (bytes/sec): 1886491648/2948
Max sent sequence-number: 42
UDP encapsulation used for NAT traversal: N
[Inbound ESP SAs]
SPI: 3594384061 (0xd63df2bd)
Proposal: ESP-ENCRYPT-DES-64 ESP-AUTH-MD5
SA remaining key duration (bytes/sec): 1887433300/2948
Max received sequence-number: 40
Anti-replay window size: 32
UDP encapsulation used for NAT traversal: N
